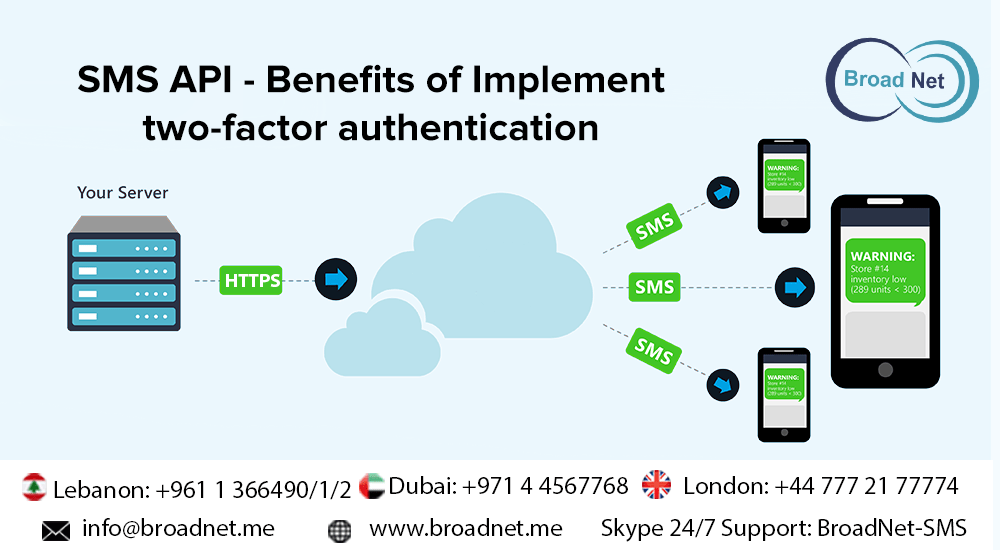
Traditionally the humble password was regarded to be fair enough security measure partly because hackers were learners, key loggers and social theft parties were not matured enough or did not have the technical know-how to conduct an organized theft into one’s privacy and system. However, as you know today is not yesterday. As the technologies advance, new ways to invade into your system has emerged. And that’s why you need to leverage on the benefits of two factor authentification.
Two factor authentification or 2FA in short is the method of adding an extra layer of protection before a user logs on into a website, system or processes. To understand how it works, you need to understand how it authenticates a user. There are presently three ways to do that –
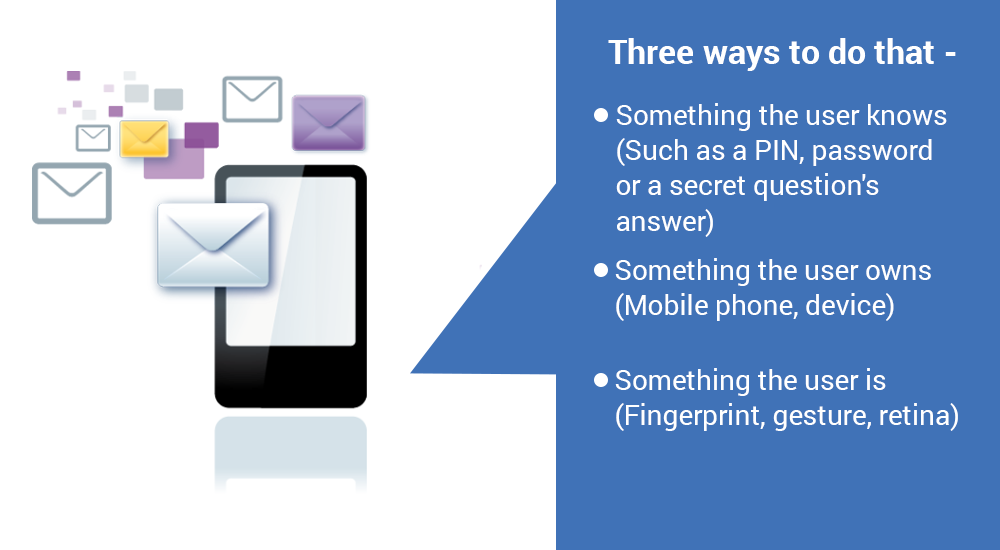
- Something the user knows (Such as a PIN, password or a secret question’s answer)
- Something the user owns (Mobile phone, device)
- Something the user is (Fingerprint, gesture, retina)
Two-factor authentification is the combination of any two of the above-mentioned ways. Using the above ways; such as by sending a code to a mobile, asking to reenter the password sent on email, mobile, PC, or using a user’s fingerprint; the actual authentification of the user can be known. The authentification code can be sent on SMS, Email (Blackberry Secure email delivery), voice, Smart phone Soft Token application, P.C. or Mac OS Soft Token application. Simple as this!
Therefore; two factor authentification works in a number of ways; helping you channelize your entire process, and safeguarding your privacy. The rise of password theft and other issues have made it relatively essential for you to leverage on the importance of two-factor authentification. The entire process of developing password and sending standalone code is this important.