SIM BOX Detection
Mobile Operator Revenue Challenges & Opportunities
Revenue Landscape
A2P Risk Analysis
Market Dynamics
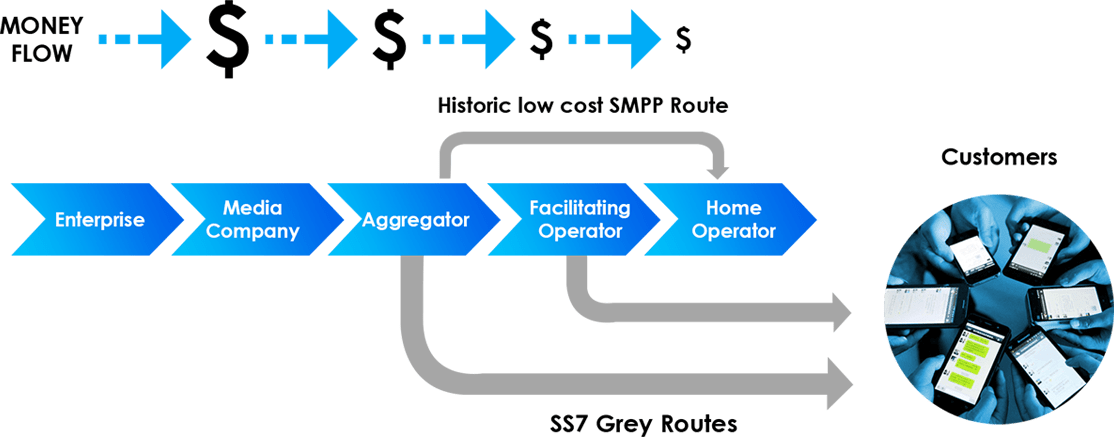
Complex relationships between operators, aggregators, and VARs create revenue vulnerabilities in the A2P ecosystem.
Fraud Vectors
Exploitation of unlimited SMS bundles, repurposing of P2P packages for A2P traffic, and billing system weaknesses across global markets threaten revenue security.
Industry Impact
Major operators like China Mobile and Vodafone India face revenue threats when generous SMS packages are exploited for fraudulent A2P messaging.
Business Risk
This exploitation creates direct revenue loss from fraudulent traffic and degrades service quality, undermining A2P market stability.

Revenue Protection Strategy
The Threat
SIM box fraud diverts A2P traffic through consumer SIM cards, exploiting unlimited SMS plans to bypass operator fees.
Key Challenges
Multiple SIM cards managed via automated systems, high-volume message transmission, mix of spam and legitimate traffic, advanced evasion techniques, and rapid SIM rotation complicate detection efforts.
Impact
These fraudulent activities result in direct revenue loss, network congestion, quality degradation, and market destabilization.
Solution Requirements
Modern fraud prevention demands sophisticated detection systems with multi-layer monitoring, real-time analysis, pattern recognition, automated response, and continuous adaptation.

A2P Fraud Prevention Strategy
Comabtting Fraud

Policy Controls
Establish clear fair usage policies for SMS bundles, restrict bundles to P2P communications only, monitor compliance actively and systematically, and update terms based on emerging threats.
Detection Systems
Implement real-time traffic analysis, conduct regular billing audits, perform system penetration testing, deploy advanced SMS firewalls, and monitor network patterns continuously.
Smart Protection
Utilize machine learning for threat detection, maintain current threat intelligence database, enable automated threat response, track emerging fraud patterns, and adapt security measures continuously.
Integrated Approach
Combine multiple detection techniques, coordinate policy and technology solutions, enable rapid response capabilities, update protection strategies regularly, and share threat intelligence across systems.


